Online privacy is the need of the times. In particular, when there is a continuous increase in the number of user data stealing techniques. Recognizing this demand, large online messaging services use a technique called terminal encryption, to secure and protect user conversations.
But what does the end encryption mean and how does it actually work? Find the answer through the following article!
Learn basic about encryption
Encryption means converting information into code, hiding the true meaning of information.
Decoding means converting this code back to the original information and returning its meaning. It is the reversal mechanism of encryption.
Why do you need encryption?
When you send a certain content online, it may be messages, comments or images – they bring some “information”. What we need to understand is that this message or image is not valuable – but valuable about the information it provides. It is valid for the information that one can interpret when seeing it. So what will happen if the message or image you are sending is also seen by the third person through the Internet? They will know the information you are trying to convey. What about the use of encryption and decoding? This is the time when the terminal encoding is effective.
What is terminal encryption?
You encrypt messages/images to be sent and it switches to the Internet as a 'secret' code. Then only the recipient can decode this 'secret' code. This process is called the terminal encryption.
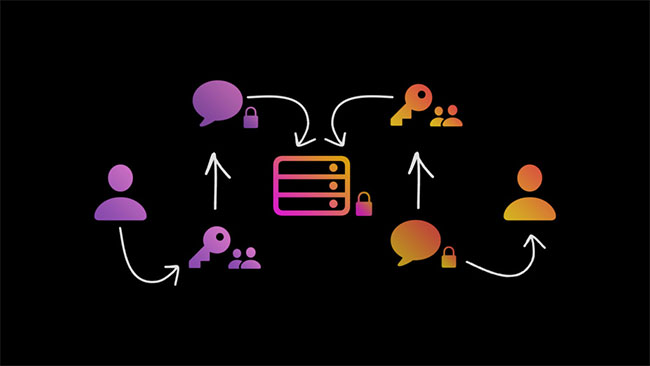
In the simplest way, the terminal encryption ensures a secret communication between the sender and the recipient, preventing third parties from accessing this information. The tools and technology help to perform this process are designed into messaging applications and software that users (may) use.
What is the terminal encryption?
The goal of terminal encryption is to prevent any invaders stealing information between the sender and the recipient. Back to the previous situation: You are sending others a message.
When using the terminal encryption service, you are provided with a pair of public and private key. These key help you encrypt and decode. Along with that, the messaging app has an algorithm, including mathematical functions used to encrypt or decode data.
When you are sending a message to others, you will be provided with a peasure of mapping to that person's chat box. Public Key is used to encrypt messages, using the algorithm in the messaging app. This public key helps you recognize the recipient's device and the fact that he will receive a message.
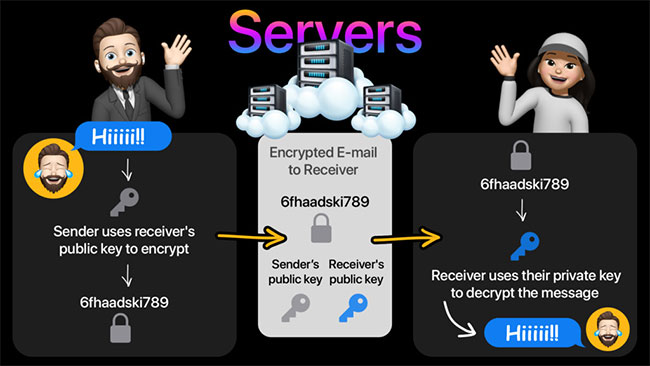
Now, the recipient will use the private key, help decipher the message and interpret information in the message you sent. This private key is only available and for the recipient's device. Therefore, no one else can decode the message – at this time, the end of the end encryption has been successful.
This is the basic operating principle of terminal encryption. However, not all services use terminal encryption. Some tools often use replacement intersection techniques. So what is the difference between these two techniques.
How is the terminal encryption different from other types of encryption?
What makes the end encryption unique compared to other encryption systems is only the end point – the sender and the recipient – is able to decipher and read the message. Symmetrical lock encryption, also known as single -lock encryption or secret lock, also provides a continuous encryption layer from the sender to the recipient, but it only uses one key to encrypt the message.
The lock used in an encryption for a key can be a password, code or a series of randomly created and sent to the recipient, allowing them to decode the message. It can be complicated and makes the message look meaningless to intermediaries. However, the message may be blocked, decoded and read, no matter how strong the course changes if an intermediary holds the key. End encryption, with two locks, can prevent intermediaries from accessing the lock and decoding the message.

Another standard encryption strategy is encryption during transportation. In this strategy, the message is coded and decoded by the sender at an intermediary – a third party server owned by a messaging service provider – then re -encrypted and send to the recipient. The message cannot be read during the transmission process and can use the two -lock encryption but it does not use the two -end encryption because the message has been decoded before reaching the last recipient.
Encrypting during the transmission process, such as the end of the end, helps the message not to be blocked on their journey, but it creates hidden holes in the middle of the place where they are decoded. Transport coding protocol layer security is an example of encryption during transportation.
What is the difference between the terminal encryption and the interface encryption?
As mentioned earlier, not all services are encrypted for terminals. But, that doesn't mean they don't have any encryption. The most common coding form for websites is TLS encryption – Transport layer security.
The only difference between this type of encryption and terminal encryption is in TLS, the encryption process takes place in the sender's device and is decoded at the server. Therefore, it is not really encoded but provides good security levels and has the ability to protect user information.
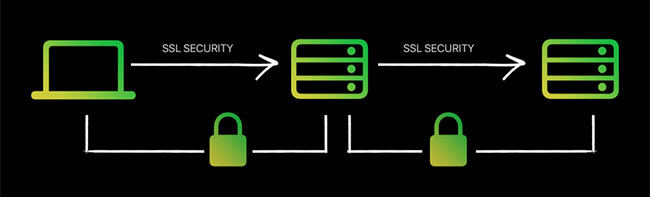
It is also known as encryption when transferred. This means that service providers can access all your messages through their server. That's why you can easily see your old Instagram messages when you download the application again, but not on WhatsApp. You can only recover the message by downloading the backup file and decipher it on your device.
How is the terminal encryption used?
The terminal encryption is used when data security is needed, including in the financial, health and communication industry. It is often used to help companies comply with rules and laws on privacy and data security.
For example, the electronic POS system supplier will put E2ee into its product to protect sensitive information, such as customer credit card data. The included E2EE will also help retailers comply with the payment of payment card data (PCI DSS), stipulating that the card number, magnetic strip data and security code are not stored on the guest device.
What is the end -to -end encryption against?
E2ee protects against the following two threats:
- The curious eyes. E2ee prevents anyone other than the sender and the recipient planning to read the message information during the transmission because only the sender and the recipient can lock to decipher the message. Although the message can be displayed with an intermediary server that is helping to transfer the message, it will not be able to read.
- Fake. E2EE also protects against coding messages. There is no way to predict the change of encrypted messages in this way, so all changing efforts are meaningless.
What does the terminal encryption does not protect?
Although the E2EE key exchange is thought to be unable to break by known algorithms and current calculation power, there are some hidden weaknesses that have been determined in the encryption diagram, including the following 3 points. :
- Metadata. Although E2ee protects the information inside the message, it does not hide the information about the message, such as the date and time of sending or the participants. This super data can make bad people interested in coded clues can block information after it is not encrypted.
- The end point is infringed. If one of the last two points is infringed, the attacker can see the message before it is encrypted or after being decoded. The attackers can also take the lock from the ends of intrusion and perform an intermediary attack with the stolen common lock.
- Intermediate parties are easily attacked. Sometimes, suppliers claim to provide end encryption while what they really brings are similar to the encryption during the transmission process. The data can be stored on an intermediary server where it may be illegally accessed.
Advantages and disadvantages of terminal encryption
Here are some advantages of terminal encryption.
- Each step is completely protected.
- Servers of messaging services cannot access messages and relevant information.
- Information cannot be accessed by people who do not have online authority.
- You cannot recover the message through a new login – unless the backup is encrypted. Consider examples of Instagram and WhatsApp Messenger messaging programs explained above.
Some disadvantages of terminal encoding include:
- Super data like the day, time and the name of the participant are not encrypted.
- If the endpoint (senders or recipients) are easily attacked, then the terminal encryption does not have much effect.
- In some cases, there may be a Man-in-The-Middle attack, despite the terminal encryption. Therefore, if someone chooses to impersonate the sender or the recipient in a physical way, the outsiders want to read the messages and information.
Above are all the advantages and disadvantages of terminal encoding. If you are still wondering if you should turn the end encryption even if you don't send a secret message, then the answer is yes. Why allows others to access your data?
Some common ending messaging applications
Here are some of the best ending messaging applications for iPhone and Android. You can use any of the following ways to add security layers for your message.
1. WhatsApp messaging tool
The very popular WhatsApp messaging tool supports terminal encryption. You can use the links below to download and install for both iPhone and Android.
2. Private Signal messaging tool
Signal is an encrypted messaging application, rich in other features for iPhone and Android. It provides a more modern user interface than WhatsApp.
Download Signal for iPhone to download Signal for Android
3. IMessage
iMessage, as we all know, is the basic messaging app for all Apple users. All messages and files on iMessage are encoded. However, it does not work multi -platform and therefore, is not available for Android.
4. Telegram
Telegram is another feature -rich messaging application that we all want to use as the main messaging application and want all WhatsApp users to switch to this application. It provides terminal encryption, although on the basis of the option. This option is called “Secret Chat”.
It is all the popular applications that the article can propose to encrypt private private messages.
This is all you need to know about the terminal encryption. Hope you find this article helpful!



