If you want to browse the dark web, go first to Tor Browser. However, Tor Browser can be dangerous if used incorrectly – but there are ways you can use it safely.
1. Use Tor's most secure security mode

Tor has 3 default security modes: Standard, Safer and Safest. Standard Do not disable any features. Regime Safer disables the most dangerous website features, while Safest mode blocks everything but the basic website features.
You can enable Tor's Safest mode by performing the following steps:
- Open Tor settings.
- Navigate to Privacy and Security.
- Scroll to Security:and select Safest from the list of options.
Once activated, your dark web browsing experience will be much safer.
2. Update Tor regularly
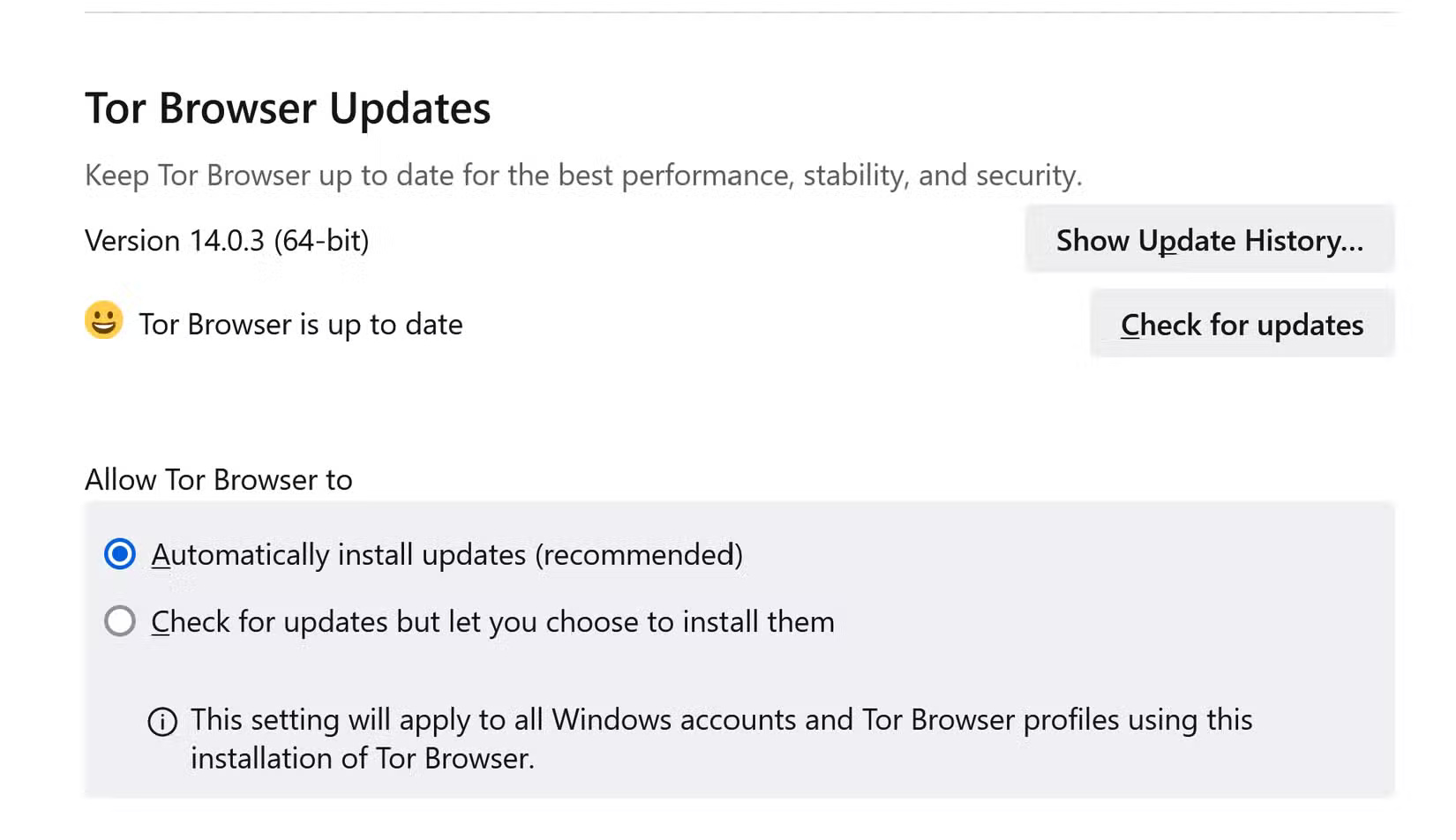
You should also update Tor regularly. If you're using an older version of Tor, you may be exposed to vulnerabilities that criminals have discovered. Updating ensures that you have the latest patches.
If an update is available, you can update it by opening the main menu (≡) and clicking Update available — restart now. You can also update manually by uninstalling Tor Browser and reinstalling it using the latest release from the Tor website.
Tips: You can also manually check for updates by clicking the button Check for updates in Menu (|||) > Settings > General > Tor Browser Updates.
3. Do not use personal accounts on Tor
If you want to keep your identity on Tor a secret, you should be careful when using a personal account. You should never log into a personal account during a session of any activity that you want to keep private.
Tor Browser clears cookies, browsing history, and cached web content at the end of each session – so if you close and reopen Tor, you don't need to worry about your activity being linked.
4. Don't worry about resizing the Tor window
Previously, resizing your Tor window could endanger your privacy because of a practice known as “fingerprinting.” Characteristics like your window resolution can be combined with other characteristics to “define you” or at least to differentiate you from the masses.
Nowadays, that's no longer a concern because Tor Browser uses a technique called “letterboxing,” which involves adding margins to the browser window to keep you within one of a few large user groups. . In other words, you get good resolution for your screen size while remaining anonymous.
5. Don't customize Tor
While resizing the Tor window is fine, you should still avoid customizing Tor in other ways. Installing any add-on will set your browser apart from others (especially if you install a lot of add-ons), so you should avoid doing so whenever possible.
You should not change configuration options other than for your own safety unless there is a good reason to do so. Small changes are often insignificant, but they come with the risk of giving the browser a unique identifier. Overall, browsing on Safest is enough to protect you.
6. Don't share PII or reuse usernames on Tor
While it might be controversial to reuse your username or share your phone number with regular Internet retailers, those practices are impossible when browsing the dark web. Different rules apply and anything that could end your anonymity is not allowed.
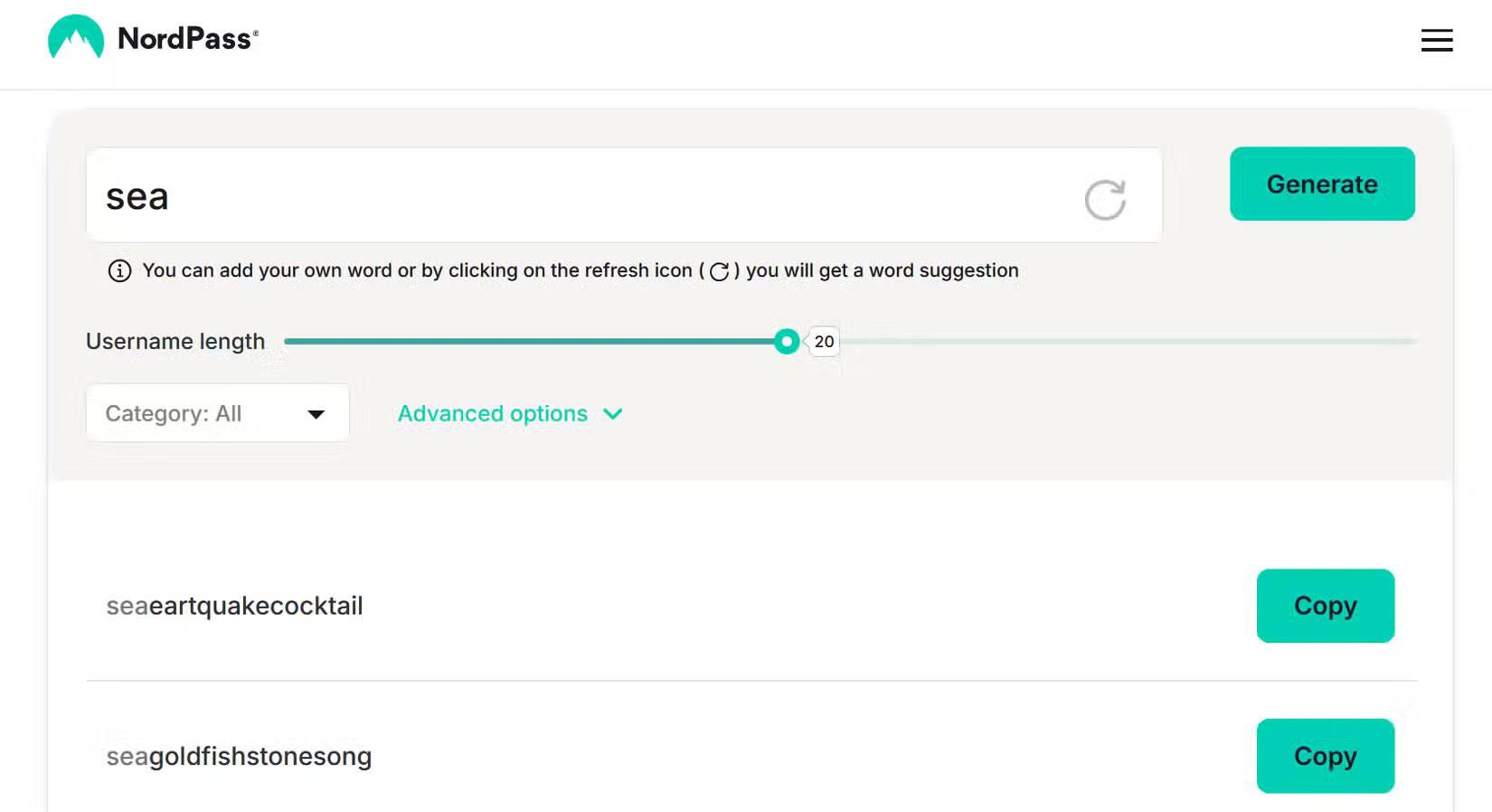
It's a good idea to come up with unique usernames that don't suggest anything about you when you need to create an account (such as for anonymous email). Username generators like those offered by NordPass can help.
Before sharing any information about yourself, you should ask if you have a good reason for doing so. You should try to share as little information about yourself as possible.
Warning: It is important to read about what personally identifiable information (PII) is before using Tor if you want to prevent any accidental disclosure.
7. Be careful when using VPN with Tor!

Despite what you may have heard, using a VPN with Tor is also generally not recommended. This rule is not set in stone, and Tor clearly states that you can use both together if you are an advanced user who can configure them in a way that does not compromise your privacy.
If you don't know how to configure the two apps, a VPN can do more harm than good. Your ISP and router already know when you connect to Tor, and introducing another third party can also be risky. On the plus side, connecting a VPN to Tor hides your browser usage from your ISP.
Note: If you must use a VPN, configure it properly and choose a VPN that will keep your information truly safe.
8. Be careful with files from Tor

You should be careful with any files you download from the web, and that's doubly important when browsing on Tor. You will need to take steps to verify the authenticity of the files you download before considering opening or running them.
If a signature file (.asc) is provided, you can verify the authenticity of the signature using GnuPG. You can also check the file in your antivirus software, run the file in an isolated environment like a virtual machine, or upload the file to a website like VirusTotal to check for any known malware.
9. Remember that Tor is not a protection measure
Most importantly, you should remember that Tor Browser is not a protection measure – it is just a browser that provides privacy. By combining good browsing practices with the most secure settings on Tor, you can keep yourself safe when browsing the dark web. But you should never take any risks without knowing how to protect yourself.



