Wireguard is a powerful open source virtual private network (VPN) daemon that can run on both desktop and mobile devices. It offers a fast and lightweight alternative to traditional VPNs like IPsec and OpenVPN. Today's article will show you how to install Wireguard and create a simple VPN setup using 3 Linux machines.
Why use Wireguard as a VPN solution?
One of the biggest advantages of Wireguard is that it is a fast and lightweight VPN daemon. Unlike traditional solutions, Wireguard does not add much cost to your network. This results in lower latency and high overall throughput on your nodes.
Another key feature of Wireguard is that it is a module within the Linux kernel. This allows it to run without taking up any additional system resources from your computer, making it an ideal choice for deployment on low-end devices and SOCs.
Finally, Wireguard also leverages modern encryption standards and development practices. It also has multiple formal verifications, confirming the correctness of the code, ensuring security and resistance to Wireguard attacks.
Download Wireguard
The first step to setting up Wireguard on Linux is to download its core tools from the distribution's repository. This allows you to control the built-in Wireguard kernel module using userspace commands.
To install core tools in Ubuntu and Debian, run the following command:
sudo apt install wireguard wireguard-toolsIn Fedora you can use the dnf package manager:
sudo dnf install wireguard-toolsFor Arch Linux, you can run pacman to load Wireguard's core tools:
sudo pacman -S wireguard-toolsConfirm that you have correctly installed the Wireguard tools by loading its help screen:
wg -h
Set up Wireguard server
Assumption: This article assumes that you are installing the Wireguard server on a Linux system with a publicly accessible IPv4 address. The instructions will still work on the server behind a NAT, but it will not find nodes outside of its subnet.
With the Wireguard core toolkit on your Linux machine, you can now set up a VPN server node. This node will act as the Internet gateway for client nodes in the network.
Start by navigating to the Wireguard configuration folder and setting its default permissions to “root only”:
cd /etc/wireguard
sudo umask 077Note: Some systems may prevent you from accessing the “/etc/wireguard” directory as a regular user. To fix that, switch to root user with sudo -s.
Create public and private keys for Wireguard server:
sudo sh -c 'wg genkey | tee /etc/wireguard/server-private-key | wg pubkey > /etc/wireguard/server-public-key'Create a server configuration file using your favorite text editor:
sudo nano /etc/wireguard/wg0.confPaste the following code block into the server configuration file:
[Interface]
PrivateKey = PASTE-YOUR-SERVER-PRIVATE-KEY-HERE
Address = 10.0.0.1/32
ListenPort = 60101
PostUp = iptables -t nat -I POSTROUTING -o NETWORK-INTERFACE-HERE -j MASQUERADE
PostDown = iptables -t nat -D POSTROUTING -o NETWORK-INTERFACE-HERE -j MASQUERADEOpen a new terminal session, then print the server's Wireguard private key:
sudo cat /etc/wireguard/server-private-keyCopy the server's private key to the clipboard.
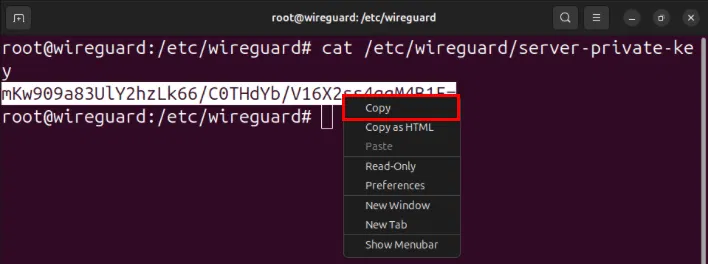
Replace the value of the variable PrivateKey with the key on the clipboard.
Find the network interface that has Internet access using the ip command:
ip route get 8.8.8.8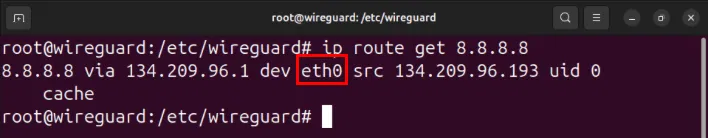
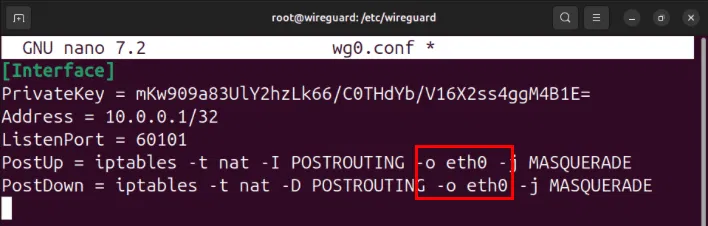
Set the value of the -o flag on both the PostUp and PostDown variables to an interface with Internet access, then save the configuration file.
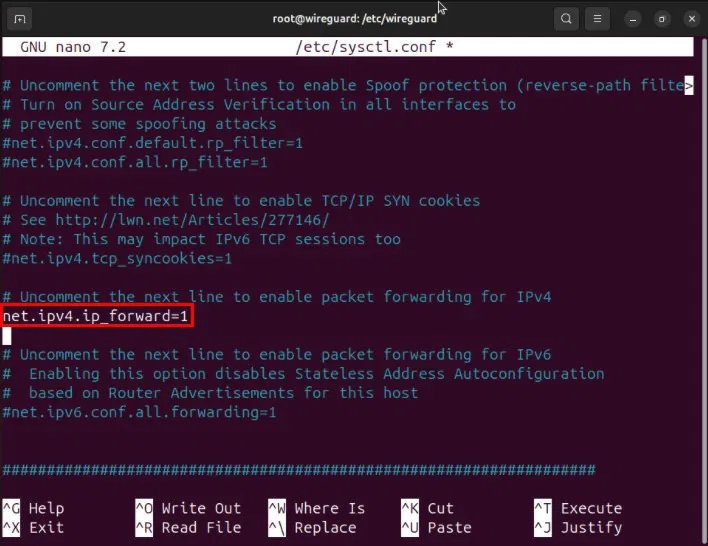
Open the server's “/etc/sysctl.conf” file with your favorite text editor:
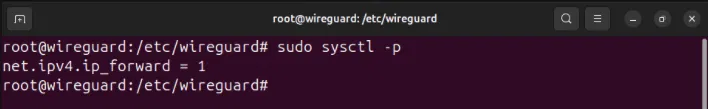
sudo nano /etc/sysctl.confScroll down to the containing line net.ipv4.ip_forward=1then remove the pound sign (#) in front.
Reload the new sysctl configuration by running: sudo sysctl -p.
Set up and connect the Wireguard client
You now have a properly configured Wireguard server without any peers. To use it, you need to set up and connect your first Wireguard client.
Navigate to the client system's Wireguard configuration directory and set its default permissions:
cd /etc/wireguard
sudo umask 077Create the client's Wireguard key pair with the following command:
sudo sh -c 'wg genkey | tee /etc/wireguard/client1-private-key | wg pubkey > /etc/wireguard/client1-public-key'Create the client's Wireguard configuration file using your favorite text editor:
sudo nano /etc/wireguard/wg0.confPaste the following code block into the client configuration file:
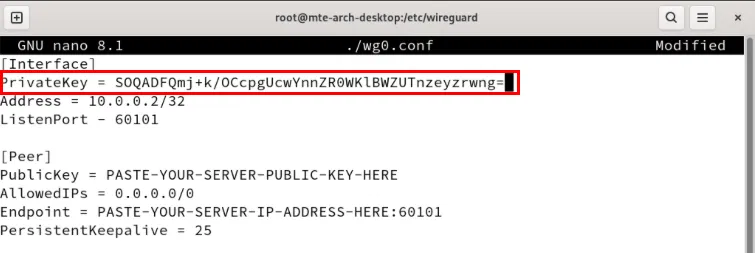
[Interface]
PrivateKey = PASTE-YOUR-CLIENT1-PRIVATE-KEY-HERE
Address = 10.0.0.2/32
ListenPort = 60101
[Peer]
PublicKey = PASTE-YOUR-SERVER-PUBLIC-KEY-HERE
AllowedIPs = 0.0.0.0/0
Endpoint = PASTE-YOUR-SERVER-IP-ADDRESS-HERE:60101
PersistentKeepalive = 25Replace the PrivateKey variable with the client's private key.
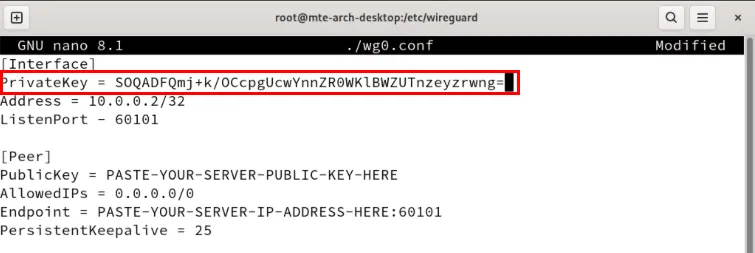
Open the Wireguard server's terminal session, then print its public key:
sudo cat /etc/wireguard/server-public-keySet the value of the PublicKey variable to the server's public key.
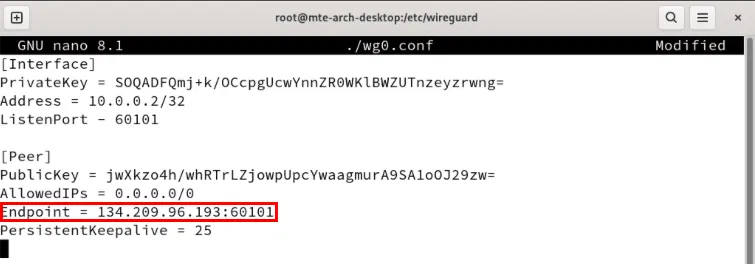
Change the Endpoint variable to the IP address of the Wireguard server.
Save the configuration file, then use the wg-quick command to start the Wireguard client:
sudo wg-quick up wg0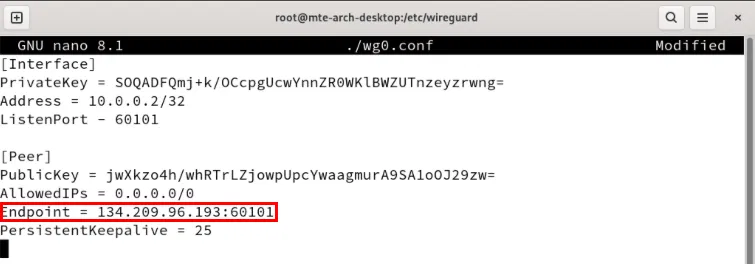
Note: This command will disable the client's network connection until you start the Wireguard server. To return to the original network, run sudo wg-quick down wg0.
Link the Wireguard server to the client
Access the Wireguard server's terminal session, then open the server's configuration file:
sudo nano /etc/wireguard/wg0.confPaste the following block of code after the section [Interface]:
[Peer]
PublicKey = PASTE-YOUR-CLIENT1-PUBLIC-KEY-HERE
AllowedIPs = 10.0.0.2/32
PersistentKeepalive = 25Set the PublicKey variable to the Wireguard client's public key.
![Location of the block [Peer] and the client's public key.](https://st.quantrimang.com/photos/image/2024/08/06/thiet-lap-wireguard-vpn-tren-linux-12.jpg)
Note: You can get the public key by running sudo cat /etc/wireguard/client1-public-key on your client.
Save the configuration file, then run the following command to start the Wireguard service on the server:
sudo wg-quick up wg0Add a second client to the server
A key feature of any VPN service is that it can link multiple machines from different networks. This feature is useful if you have computers in different locations or want to host a private game server for friends.
To do this in Wireguard, you need to create a configuration file for the new VPN interface on your server. The easiest way to do this is to copy the current server configuration and give the copy a new name:
sudo cp /etc/wireguard/wg0.conf /etc/wireguard/wg1.confOpen your new configuration file with your favorite text editor:
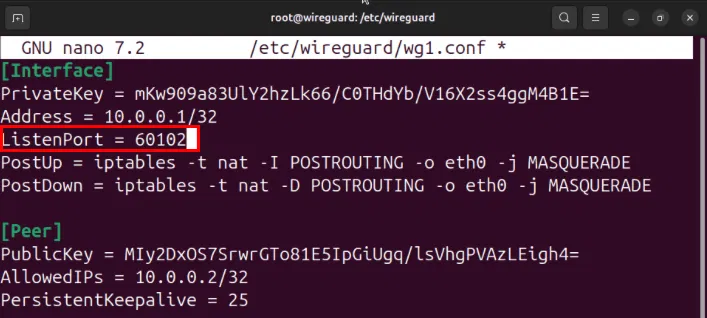
sudo nano /etc/wireguard/wg1.confSet variable ListenPort wall 60102. Doing this will prevent any port conflicts between VPN interfaces wg0 and wg1.
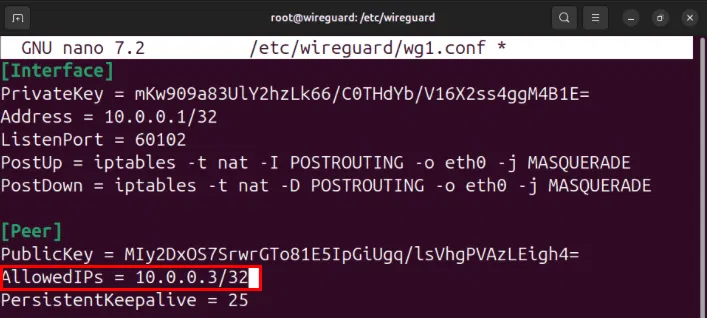
Go to section [Peer] and change variables AllowedIPs from “10.0.0.2/32” wall “10.0.0.3/32”then save your configuration file.
Configure the second Wireguard client
Log in to the second machine, then prepare your Wireguard configuration folder:
cd /etc/wireguard
sudo umask 077Create a new Wireguard key pair with the following command:
sudo sh -c 'wg genkey | tee /etc/wireguard/client2-private-key | wg pubkey > /etc/wireguard/client2-public-key'Create a new configuration file using your favorite text editor:
sudo nano /etc/wireguard/wg0.confPaste the following code block into the new configuration file:
[Interface]
PrivateKey = PASTE-YOUR-CLIENT2-PRIVATE-KEY-HERE
Address = 10.0.0.3/32
ListenPort = 60102
[Peer]
PublicKey = PASTE-YOUR-SERVER-PUBLIC-KEY-HERE
AllowedIPs = 0.0.0.0/0
Endpoint = PASTE-YOUR-SERVER-IP-ADDRESS-HERE:60102
PersistentKeepalive = 25Set variable PrivateKey into the private key of the second machine, then change the variable PublicKey into the server's public key.
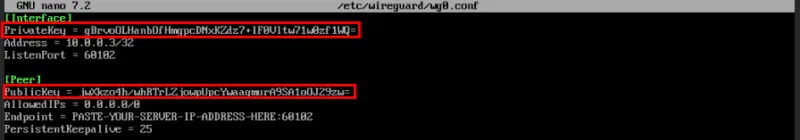
Variable substitution Endpoint by the server's IP address, followed by “:60102”.
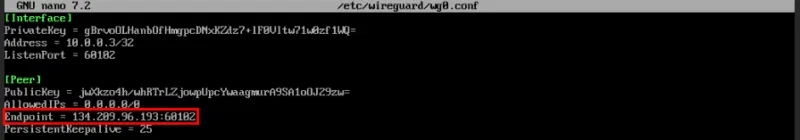
Save your configuration file, then start the second machine's Wireguard client:
sudo wg-quick up wg0Associate the second client with the Wireguard server
Log back into the Wireguard server, then open the VPN interface configuration for your second client:
sudo nano /etc/wireguard/wg1.confScroll down to the section [Peer]then replace the variable PublicKey with the second client's public key.
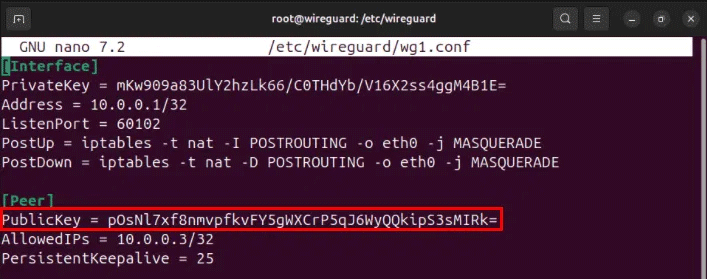
Save your configuration file, then start the second VPN interface with the wg-quick command:
sudo wg-quick up wg1Confirm that your first and second Wireguard clients are displaying correctly on the server by running wg.
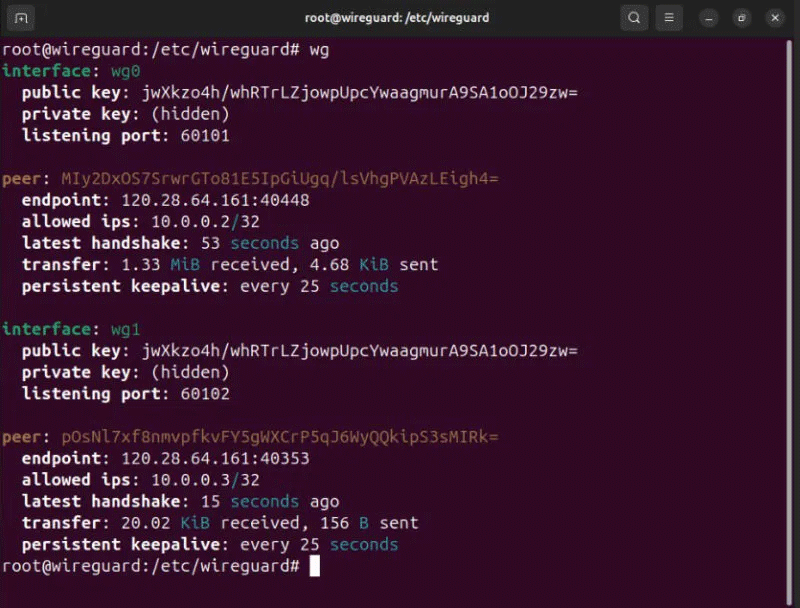
Check the Wireguard network
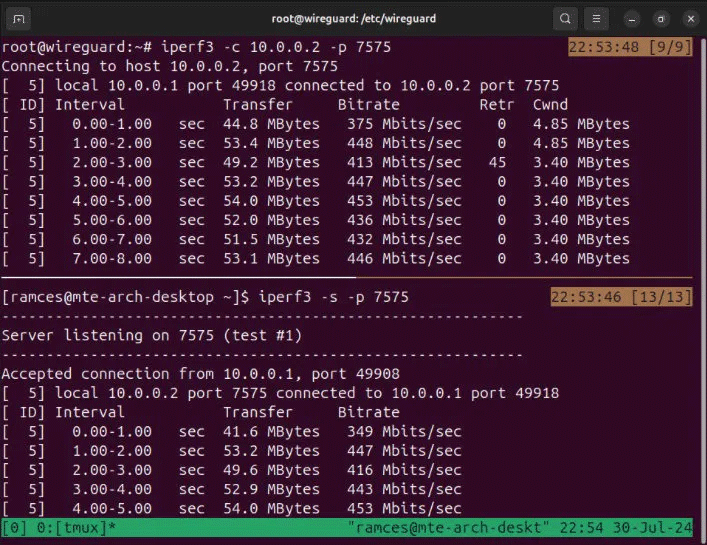
With both the server and client on the Wireguard network, you can now test connectivity and latency between your nodes. To do this, make sure you have network diagnostic tools installed on the system:
sudo apt install net-tools curlIn Fedora, you only need to install curl because it has network tools available right out of the box:
sudo dnf install curlFor Arch Linux, you can use pacman to install curl and networking tools:
sudo pacman -S traceroute curlStart by tracing the route of a packet between two clients. The following shows how an IP packet goes from “10.0.0.2” to “10.0.0.3:”
traceroute 10.0.0.3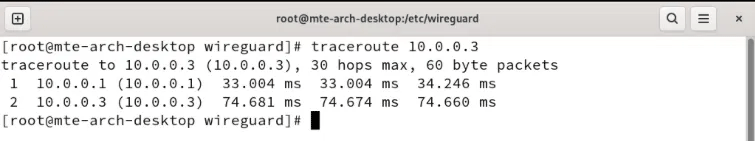
Check if any of your nodes can access the public Internet by pinging a public IP address:
ping -c 5 8.8.8.8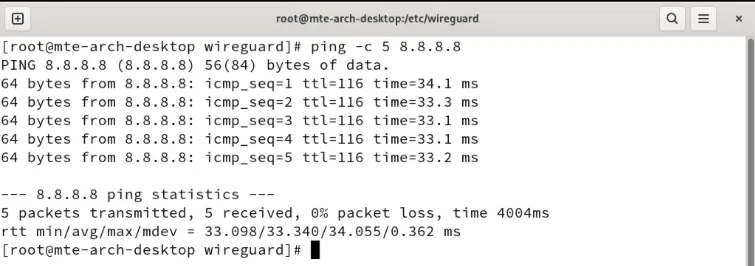
Finally, confirm that your nodes share the same public IP address as your Wireguard server:
curl ipinfo.io/ip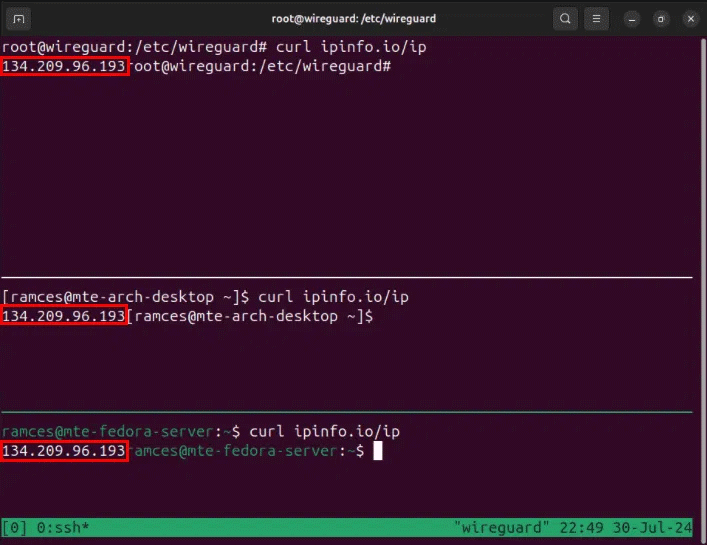
Learning how to set up a Wireguard network on Linux is the first step to exploring the fascinating world of VPNs. Let's dig deeper and see our picks for the best security-focused VPN providers you can get today.



